Our Key Clients






















DevSecOps market size to reach USD 23.42 billion in 2028. Rising need for repeatable and adaptive processes and increasing need for custom code security are key factors driving industry demand.
The Challenge
DevSecOps can be extremely beneficial, improving both security and organizational efficiency. However, the most challenging part of DevSecOps adoption is to make security complement existing business processes, culture, and people, in addition to the complexities in the cloud. With Vulnerability attacks on the rise, it’s time for application security teams to get a move on— from appsec after the fact to secure code throughout the software development life cycle. Due to a lack of shared responsibility and no standard operating procedures, low utilization and ROI on security tools, security testing is mostly performed as a last mile activity before go-live. A few specific challenges include:
- Comprehensive treatment for enterprise-wide Security Risks might not be possible resulting in Compliance/Regulatory issues that can lead to significant erosion of Brand Value and Trust
- Late identification of security risks might result in additional verification and validation cycles leading to Long lead times to production
- Only limited Security Risks can be accounted before go-live resulting in significant re-work and higher cost of service maintenance
- There is limited verification & validation across apps/services leading to lower efficiencies as most of the security activities are not integrated
- Post-Production, SecOps Team etc. spend at least 4 hrs per security alert on triaging, correlating, risk relating, writing up and retesting
- Development team takes on an average 10 hrs to remediate security issues found in production
- It takes 90 days on an average to remediate all or serious vulnerability once they have been detected
DevSecOps
DevSecOps is considered transformational in Gartner Hype Cycle, 2022. API attacks have resulted in an endless stream of data breaches and other security incidents, yielding significant damages to organizations and individuals. As a consequence, DevSecOps teams, along with business leaders, are increasingly interested in API testing and Security. The innovations of DevSecOps and software composition analysis are on the verge of gaining mainstream adoption.
DevSecOps, also referred to as SecDevOps and DevOpsSec, brings the security aspect of a software development process in spotlight. By sealing any potential gaps, DevSecOps leak-proofs an application through regular risk assessment. It activates data protection and ensures optimal compliance by analyzing written codes, modeling potential threats, and imparting required security training. For companies still in the planning stages of DevSecOps, improving security and time to market are the top two drivers for adoption, but as the approach takes hold across application builds, quality, and resilience become the stand-out reason why it flourishes.
We believe that Security is Everyone’s Responsibility, and it spans Security Engineering, Security Governance, Security Automation, and Security Awareness. Following are our foundational themes:
Security Engineering
- Security requirements Risk analysis
- Architecture and Design reviews
- Threat modelling
- Shift-left test adoption
- Functional application security testing
- End-to-End vulnerability management
- Manual penetration testing
Security Governance
- Metrics and Measurement
- Quality gates
- Defined roles and responsibilities
- Defined SLAs and KPIs
- Standardized reporting and escalation
- Application wise security score cards
- Executive Risk/Compliances dashboards
- Vulnerability categorization & prioritization
Security Automation
- Automated source code analysis
- Dynamic Analysis
- Automated penetration tests
- CI/CD pipeline integration
- Continuous monitoring of production systems
- Automated Alerts & Rapid Feedback mechanism
- Automated Incident Resolution
Security Awareness
- Learning Management System for training:
- Latest security trends and vulnerabilities
- Security best practices and coding guidelines
- Continuous skill assessments
- Developer trainings
Our Partnerships
Cigniti has meaningful strategic vendor relationship, partnering with leaders such as: Checkmarx, Veracode, and Github.



Tackling the Maze ransomware attack with security testing
Financial Application Security Testing for US Automobile financing firm
Security Testing and Vulnerability Assessment Tools – Learnings and Experiences
CyberSecurity Assurance Program (CSAP) Services
As part of our CyberSecurity Assurance Program (CSAP) for Enterprises, we conduct and provide the following services:
- Security Requirements Analysis
- Architectural review
- Threat Modelling & Threat Assessments
- Static Application Security Testing
- Dynamic Application Security Testing
- Mobile Application Security Testing
- Vulnerability Assessment & Penetration Testing
Our focus areas are Processes and Practices, Governance, Tools, and Integration and Automation.
The Solution
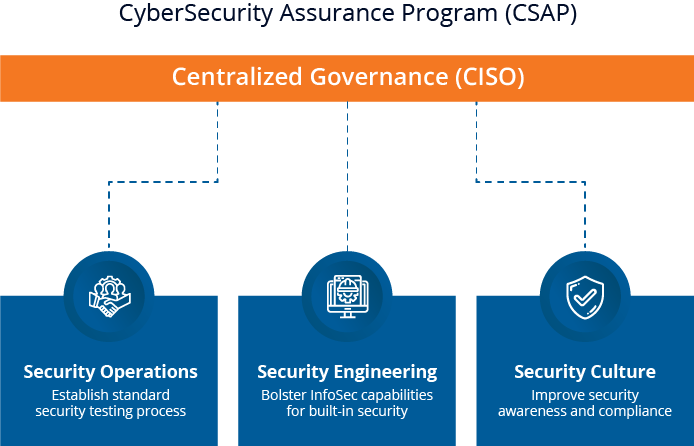
A holistic enterprise Security Assurance program matures and stabilizes overall security testing capabilities in terms of people, process, and tools, and delivers a secure development lifecycle. It addresses Operating Model, Capability, Culture, Technology Platforms, & Governance.
We perform an in-depth assessment of the current InfoSec organization across testing practices, automation, tech stack, tool usage, metrics and provide findings with detailed implementation roadmap.
This helps:
- Promote a collaborative and proactive culture
- Increase the team’s capability by conducting roles specific trainings
- Integrate security into the software delivery lifecycle
- Roll-out platforms that support increased automation
- Establish Test Lab’s to support on-demand verification & validation
- Establish a Metrics & Measurement framework to support insights driven improvements
- Generate an enterprise-wide balanced scorecard (risks, coverage velocity, agility & automation)
We help implement practices such as Security Requirements Engineering & Risk-Driven Design, Secure Code Implementation, Risk-Driven Testing, Secure Deployments and Operations that support security assurance and compliance requirements.
Our Differentiators
Benefits of CyberSecurity Assurance Program

Contact Us
Consult our experienced team of Cybersecurity Assurance experts today!