Cloud Migration – Security Risks and How to Mitigate Them | Cloud Migration Assurance
Cloud computing is an innovation that has witnessed tremendous growth in a very short time, more than any other emerging technology in the last century, due to the numerous benefits it offers that every sector and business can take advantage of.
The benefits are scalability, which balances the fluctuating workloads as per organization demands; efficiency, which otherwise organizations have to pay attention to in terms of frequent health checks and maintenance; the third one, cost savings, because organizations have clear visibility of choosing and controlling the services as per their business requirements; and the other one, security, for which most of the due diligence is taken care of by the cloud providers and makes organizations only focus on their actual business needs.
In the present situation, undoubtedly, 2020/21 witnessed the world adapting to the global pandemic and focusing more on shifting the entire organization’s resources to the cloud rather than utilizing some of the services expected to be scalable per customer demands.
In 2023, Gartner estimates global end-user spending on public clouds will reach over $599 billion, up from $421 billion in 2021 and nearly $500 billion in 2022.
It can’t be limited to a specific sector or specific industry. However, the entire next generation of organizations will focus their shift to cloud adoption on industries ranging from manufacturing to health care to entertainment and the Internet of Things.
Despite the multitude of benefits that cloud computing platforms offer, some inherent challenges and risks may arise due to known or unknown factors like lack of the right strategy, not utilizing the cloud services appropriately, and, most importantly, not applying the secure controls as per the organization’s business needs and goals.
Cloud applications and data pose the same threats or risks as traditional data center applications and data. The root cause of challenges specific to cloud migration security differs due to various factors.
The most prevalent security risks that organizations should consider and plan for appropriate remediation while moving resources to the cloud are as follows.
Customers have less visibility when compared with traditional data center models
In the traditional data center model, customers have clear visibility over the various resources at each location, the proper segregation of roles, and access controls to these resources per organizational business policies.
In cloud environments, customers lose some visibility of the resources due to a lack of a migration strategy and subsequent assignment of access controls for each resource and application.
Even though resources are frequently onboard and offboard, assigning and managing controls to these resources is difficult for the IT department.
Data is always available over the public network
In contrast to traditional data center access controls where sensitive data is stored, various types of controls are enforced, ranging from locked physical locations, deploying offline servers, and isolating data networks to deploying best-in-class firewalls and taking advantage of different cryptographic methods available in organizations to protect the data.
In cloud environments, data is stored in several locations per the application needs, size, and data archiving needs.
Also, regardless of the sensitivity of the data, it is always available over the public network, increasing the attack surface.
Even though data is the only resource customers should always protect in any available cloud models, most customers fail to understand this important diligence.
On-demand provision of resources
The key benefit in cloud environments is the provision of resources and applications as per customer demand, which eases business operations seamlessly. However, it also increases the risk associated with those new resources and applications.
For example, it may spin up resources that the organizations do not need, resources that are not authorized by organization security policies, not applying proper access controls for every resource as per organization security policies, and also the risk of users using specific software which they are not supposed to use.
In large enterprise environments where resources and applications are most frequently spined-up and down, thus increasing the risks of applying proper access controls for all these resources.
Too many user roles and privileges
Cloud providers have created a massive number of user roles and permissions to make customers benefit from varying organization needs and policies and have granular control over each resource, but failing to understand and assign these roles by the organization’s IT department in line with the organization policies puts most of the applications and data at risk.
In traditional data centers, the IT department is aware of the users, roles, and access control matrix created by the department personnel, which is not the case in the cloud provider’s environment.
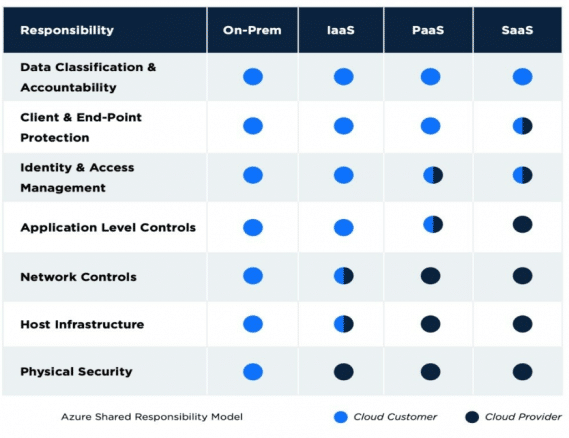
Fail to understand the shared responsibility model
Customers have flexibility in choosing specific cloud models (IAAS, PAAS, SAAS,) among various cloud providers, but most customers are unaware of responsibilities that vary depending on the chosen models.
Customers have more flexibility in choosing platforms, servers, and software specific to their business needs in the IAAS (Infrastructure-as-a-Service) model, but customer responsibilities around security are greater in this model when compared to other models; in other words, except at the physical layer, cloud customers have responsibilities at every additional layer.
In the PAAS (Platform-as-a-Service) model, customers can primarily focus on organization roles and access controls and share application-level security with the cloud provider. Cloud providers take care of all the physical and infrastructure layer security.
In the SAAS (Software-as-a-Service) model, except for customer data, the cloud provider takes full responsibility at each layer and shares some application-level access controls with customers.
If we closely notice, in any chosen cloud model, cloud customers should always have the responsibility of securing data, so organizations should not ignore the important fact that migrating their resources to the cloud doesn’t imply the duties are entirely handed over to cloud providers and customers have their responsibilities as per the chosen cloud model.
Tips to mitigate the cloud migration security risks
With proper due diligence, organizations should be able to avoid these risks by incorporating the following.
- Prepare and implement a proper migration strategy while moving resources to the cloud.
- Apply secure configuration settings for all the resources.
- Define and implement a proper access control matrix based on user roles and permissions.
- Identify and segregate all cloud resources per business criticality and apply relevant access controls.
- Apply strong data security access controls regardless of the chosen cloud model.
- Implementing standard cryptographic measures for data in rest and transit.
- Frequent rotation of cryptographic keys.
- Clearly understand and thus take up responsibilities as per the chosen cloud models.
- Do not use untrusted IAC templates for creating cloud resources.
- Run cloud configuration audit scans regularly and prioritize remediation.
Conclusion
A typical cloud assurance platform facilitates the quick assurance of data center and cloud applications and infrastructure.
The Cloud Assurance Platform helps companies improve their strategy test execution visibility, coverage, and compliance while assuring quality during secure cloud migration, data center transformation, and modernization initiatives.
A good cloud assurance platform will enable you to use a catalog-based testing approach, enable cost predictability, accelerate time-to-market, and efficiently execute infrastructure test automation.
Cigniti has a substantial body of technical and business differentiators that can help it achieve a niche in the cloud migration assurance space.
The business differentiators include independent testing services, early warning signals, and vertical-specific expertise in understanding business processes and requirements across verticals to deliver value-added solutions.
Get maximum value from your cloud transformation journey with Cigniti’s Cloud Migration Assurance services. Schedule a discussion with us to consult with our experienced team of cloud migration assurance experts.





Leave a Reply